Big tech targets cyber surveillance industry
It’s been an especially bad week for the cyber surveillance industry, especially the Israeli one
Mandi Kogosowski
| 21/12/2021
It’s been an especially bad week for the cyber surveillance industry, especially the Israeli one. Following months of negative press, lawsuits, government sanctions, and business woes, both Meta and Google have published in-depth reports which draw the curtain to expose the very insides of this top-secret industry.
(For reasons of time, space and attention span constraints, the fact that these reports are produced and published by companies that track our every move, know everything about us, and orchestrate our lives, will be discussed another time).
Let’s review.
Meta vs. “cyber mercenaries”
On Thursday, December 16th, Meta (formerly Facebook) announced that it had removed seven surveillance-for-hire entities who targeted people on its platforms in over 100 countries, blocked related infrastructure, shared findings with security researchers and policymakers, and issued Cease and Desist warnings.
“While these ‘cyber mercenaries’ often claim that their services only target criminals and terrorists, our months-long investigation concluded that targeting is in fact indiscriminate and includes journalists, dissidents, critics of authoritarian regimes, families of opposition members and human rights activists,” Meta states in its 17-page-long “Threat Report on the Surveillance-for-Hire Industry”.
“The global surveillance-for-hire industry targets people across the internet to collect intelligence, manipulate them into revealing information and compromise their devices and accounts,” says the report, which also mentions that while, in recent months, there has been a great deal of focus on NSO group (against which there is a lawsuit by Meta), “it’s important to realize that NSO is only one piece of a much broader global cyber mercenary ecosystem.”
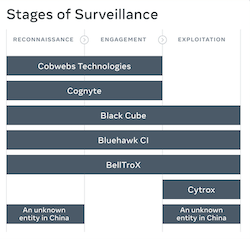
The report specifies the companies’ three-stage MO: reconnaissance (identifying potential targets and collecting information about them, mostly by using fake accounts); engagement (establishing contact with the targets or people close to the, via social engineering tactics); and exploitation (the final stage of the surveillance chain, during which the targets are tricked to give away credentials). It is noted that not all seven banned entities use the full three stages.
During that final stage, “depending on the exploit, the attacker can access any data on the target’s phone or computer, including passwords, cookies, access tokens, photos, videos, messages, address books, as well as silently activate the microphone, camera, and geo-location tracking,” says the report.
Israeli companies dominate report
Out of the seven entities, four are Israeli. They are:
-Cobwebs Technologies, with about 200 accounts removed. According to the report, “In addition to collecting information about their targets, the accounts used by Cobwebs customers also engaged in social engineering”
-Cognyte, with about 100 accounts removed. The report states that the company “sells access to its platform which enables managing fake accounts across social media platform.”
-Black Cube, with about 300 accounts removed. The company “provides surveillance services that include social engineering and intelligence gathering,” the report states, adding that it “operates fictitious personas tailored for its targets.”
-Bluehawk CI, with about 100 accounts removed. The company employed “social engineering, gathering of litigation-related intelligence about people, and managing fake accounts”, states the report.
By Meta (from the report)
The other companies are India’s BellTroX, with 400 accounts removed, most of which have been inactive for years, and used for ‘reconnaissance, social engineering and to send malicious links”; an unknown entity in China, with 100 accounts removed, which might be used by domestic law enforcement; and Cytrox, a company from North Macedonia which “develops exploits and sells surveillance tools and malware that enable its clients to compromise iOS and Android devices”.
The same day Meta published its report, Citizen Lab published one of its own, shedding some light on previously-unknown Cytrox. It states that while the company indeed got its start “as a North Macedonian start-up, a review of corporate registry documents shows that Cytrox appears to have a corporate presence in Israel and Hungary. The report suggests a link between Cytrox and Intellexa, another cyber-surveillance company founded by former IDF intelligence Unit commander, Tal Dilian.
Back to the Meta report. “The entities behind these surveillance operations are persistent, and we expect them to evolve their tactics. However, our detection systems and threat investigators, as well as other teams in the broader security community keep improving to make it harder for them to remain undetected,” state its authors Mike Dvilyanski (Head of Cyber Espionage Investigations) David Agranovich (Director, Threat Disruption) and Nathaniel Gleicher (Head of Security Policy).
“One of the most technically sophisticated exploits we've ever seen”
This wouldn’t be an article about cyber surveillance tech without discussing NSO group. And as always, there is a lot to discuss.
“Pretty incredible, and at the same time, pretty terrifying” is now Google Project Zero researchers Ian Beer and Samuel Groß described the way NSO’s zero-click spyware, Pegasus, can infect iPhones.
In a detailed, highly technical blog post published last week Wednesday, (one day before the Meta announcement), the researchers dive deep (expression borrowed from post title) into the guts of the “weapon against which there is no defense”, which just “works silently in the background”, without the victim – even a technically savvy one – ever being aware they are being targeted.
“We assess this to be one of the most technically sophisticated exploits we've ever seen, further demonstrating that the capabilities NSO provides rival those previously thought to be accessible to only a handful of nation states,” write Beer and Gross.
For their research, they used a sample of the FORCEDENTRY exploit provided by the Citizen Lab, and also collaborated with Apple (which is currently suing NSO Group).
In layman’s terms, what Pegasus basically does is exploit a vulnerability that enables the creation of fake gifs (filenames that end with .gif, but are not) in iMessages, and combines it with JBIG2 – a domain specific image codec designed to compress images. The victim’s phone only needs to receive the gif, not even open it.
“JBIG2 doesn't have scripting capabilities, but when combined with a vulnerability, it does have the ability to emulate circuits of arbitrary logic gates operating on arbitrary memory. So why not just use that to build your own computer architecture and script!?” write the researchers.
"Well, that’s what the exploit does. It uses over 70 thousand segment commands in order to “define a small computer architecture with features such as registers…and comparator which they use to search memory and perform arithmetic operations. It's not as fast as Javascript, but it's fundamentally computationally equivalent.”
More bad news for NSO
But that’s not all. For starters, there will be a part II of this blog post, which will go into additional technical details. Furthermore, this past week, it seems that NSO has generated talk all over the world – from Oregon to India, from Capitol Hill to the Zoom offices. And it does not bode well.
One day before the Google report was published, four US legislators sent a letter to the Secretaries of State and Treasury, asking them to impose sanctions on NSO Group and the other three foreign surveillance companies: the UAE’s DarkMatter, France’s Nexa Technologies and Germany’s Trovicor.
“We write to urge you to implement Global Magnitsky sanctions for technology companies that have enabled human rights abuses, including the arrests, disappearance, torture and murder of human rights activists and journalists, such as Jamal Khashoggi, by selling powerful surveillance technology to authoritarian governments,” says the letter.
18 Democratic senators and members of congress signed the letter, led by Adam Schiff (CA), Chairman of the House Permanent Select Committee on Intelligence; Gregory Meeks (NY), Chairman of the House Foreign Affairs Committee; Carolyn B. Maloney (NY), Chairwoman of the Committee on Oversight and Reform; And Ron Wyden (OR), Chairman of the Senate Committee on Finance.
And speaking of Oregon: according to the Associated Press, Oregon’s Treasurer Tobias Read is exploring legal options to terminate connections with NSO group, in it is invested via $233 million of the state employee retirement fund (via majority share owner, Novalpina Capital).
"Oregon's pension fund should not support companies like NSO, which the Biden administration recently confirmed has enabled authoritarian regimes to target journalists and human rights advocates," Wyden was quoted saying.
Spyware traces found on more activists’ phones
And there’s more: according to Israel’s Channel 12, Zoom decided to cut business ties with NSO. The company issued a statement in response, stating that “NSO decided several months ago to begin using a different and secure service that allows conference calls, video calls and more”, adding “there is no connection between between the company being put on any list and the transition that took place several months earlier.” Jeffries Financial Group has apparently also decided to resign as loan agent for NSO – which is already in danger of insolvency.
On top of all that, the Guardian reported that Pegasus was used on the phone of Indian activist Rona Wilson, a well-known prisoners’ rights activist and vocal critic of Prime Minister Narendra Modi. Forensic analysis by Amnesty International’s Security Lab (which just 10 days ago discovered that four Kazakh activists were also targeted), showed digital traces of the spyware.
Wilson has been incarcerated since 2018 due to terror-related charges. His number appeared on the global list of over 50 thousand phone numbers leaked earlier this year, which allegedly show the connection between NSO clients and potential targets, or at least people of interest.
A second Guardian report, published yesterday (Monday) claims that Pegasus was used to spy on a UN-backed investigator probing potential war crimes violations in Yemen, a Tunisian human rights activist named Kamel Jendoubi. And overnight, AP reported that two prominent Polish opposition figures, attorney Roman Giertych and prosecutor Ewa Wrzosek, also had their phones hacked by the spyware.
In light of all of this (and everything else that has happened in recent months), reports that NSO is considering nixing the Pegasus division and putting itself up for sale, should come as no surprise.
It’s been an especially bad week for the cyber surveillance industry, especially the Israeli one
It’s been an especially bad week for the cyber surveillance industry, especially the Israeli one. Following months of negative press, lawsuits, government sanctions, and business woes, both Meta and Google have published in-depth reports which draw the curtain to expose the very insides of this top-secret industry.
(For reasons of time, space and attention span constraints, the fact that these reports are produced and published by companies that track our every move, know everything about us, and orchestrate our lives, will be discussed another time).
Let’s review.
Meta vs. “cyber mercenaries”
On Thursday, December 16th, Meta (formerly Facebook) announced that it had removed seven surveillance-for-hire entities who targeted people on its platforms in over 100 countries, blocked related infrastructure, shared findings with security researchers and policymakers, and issued Cease and Desist warnings.
“While these ‘cyber mercenaries’ often claim that their services only target criminals and terrorists, our months-long investigation concluded that targeting is in fact indiscriminate and includes journalists, dissidents, critics of authoritarian regimes, families of opposition members and human rights activists,” Meta states in its 17-page-long “Threat Report on the Surveillance-for-Hire Industry”.
“The global surveillance-for-hire industry targets people across the internet to collect intelligence, manipulate them into revealing information and compromise their devices and accounts,” says the report, which also mentions that while, in recent months, there has been a great deal of focus on NSO group (against which there is a lawsuit by Meta), “it’s important to realize that NSO is only one piece of a much broader global cyber mercenary ecosystem.”
The report specifies the companies’ three-stage MO: reconnaissance (identifying potential targets and collecting information about them, mostly by using fake accounts); engagement (establishing contact with the targets or people close to the, via social engineering tactics); and exploitation (the final stage of the surveillance chain, during which the targets are tricked to give away credentials). It is noted that not all seven banned entities use the full three stages.
During that final stage, “depending on the exploit, the attacker can access any data on the target’s phone or computer, including passwords, cookies, access tokens, photos, videos, messages, address books, as well as silently activate the microphone, camera, and geo-location tracking,” says the report.
Israeli companies dominate report
Out of the seven entities, four are Israeli. They are:
-Cobwebs Technologies, with about 200 accounts removed. According to the report, “In addition to collecting information about their targets, the accounts used by Cobwebs customers also engaged in social engineering”
-Cognyte, with about 100 accounts removed. The report states that the company “sells access to its platform which enables managing fake accounts across social media platform.”
-Black Cube, with about 300 accounts removed. The company “provides surveillance services that include social engineering and intelligence gathering,” the report states, adding that it “operates fictitious personas tailored for its targets.”
-Bluehawk CI, with about 100 accounts removed. The company employed “social engineering, gathering of litigation-related intelligence about people, and managing fake accounts”, states the report.

By Meta (from the report)
The other companies are India’s BellTroX, with 400 accounts removed, most of which have been inactive for years, and used for ‘reconnaissance, social engineering and to send malicious links”; an unknown entity in China, with 100 accounts removed, which might be used by domestic law enforcement; and Cytrox, a company from North Macedonia which “develops exploits and sells surveillance tools and malware that enable its clients to compromise iOS and Android devices”.
The same day Meta published its report, Citizen Lab published one of its own, shedding some light on previously-unknown Cytrox. It states that while the company indeed got its start “as a North Macedonian start-up, a review of corporate registry documents shows that Cytrox appears to have a corporate presence in Israel and Hungary. The report suggests a link between Cytrox and Intellexa, another cyber-surveillance company founded by former IDF intelligence Unit commander, Tal Dilian.
Back to the Meta report. “The entities behind these surveillance operations are persistent, and we expect them to evolve their tactics. However, our detection systems and threat investigators, as well as other teams in the broader security community keep improving to make it harder for them to remain undetected,” state its authors Mike Dvilyanski (Head of Cyber Espionage Investigations) David Agranovich (Director, Threat Disruption) and Nathaniel Gleicher (Head of Security Policy).
“One of the most technically sophisticated exploits we've ever seen”
This wouldn’t be an article about cyber surveillance tech without discussing NSO group. And as always, there is a lot to discuss.
“Pretty incredible, and at the same time, pretty terrifying” is now Google Project Zero researchers Ian Beer and Samuel Groß described the way NSO’s zero-click spyware, Pegasus, can infect iPhones.
In a detailed, highly technical blog post published last week Wednesday, (one day before the Meta announcement), the researchers dive deep (expression borrowed from post title) into the guts of the “weapon against which there is no defense”, which just “works silently in the background”, without the victim – even a technically savvy one – ever being aware they are being targeted.
“We assess this to be one of the most technically sophisticated exploits we've ever seen, further demonstrating that the capabilities NSO provides rival those previously thought to be accessible to only a handful of nation states,” write Beer and Gross.
For their research, they used a sample of the FORCEDENTRY exploit provided by the Citizen Lab, and also collaborated with Apple (which is currently suing NSO Group).
In layman’s terms, what Pegasus basically does is exploit a vulnerability that enables the creation of fake gifs (filenames that end with .gif, but are not) in iMessages, and combines it with JBIG2 – a domain specific image codec designed to compress images. The victim’s phone only needs to receive the gif, not even open it.
“JBIG2 doesn't have scripting capabilities, but when combined with a vulnerability, it does have the ability to emulate circuits of arbitrary logic gates operating on arbitrary memory. So why not just use that to build your own computer architecture and script!?” write the researchers.
"Well, that’s what the exploit does. It uses over 70 thousand segment commands in order to “define a small computer architecture with features such as registers…and comparator which they use to search memory and perform arithmetic operations. It's not as fast as Javascript, but it's fundamentally computationally equivalent.”
More bad news for NSO
But that’s not all. For starters, there will be a part II of this blog post, which will go into additional technical details. Furthermore, this past week, it seems that NSO has generated talk all over the world – from Oregon to India, from Capitol Hill to the Zoom offices. And it does not bode well.
One day before the Google report was published, four US legislators sent a letter to the Secretaries of State and Treasury, asking them to impose sanctions on NSO Group and the other three foreign surveillance companies: the UAE’s DarkMatter, France’s Nexa Technologies and Germany’s Trovicor.
“We write to urge you to implement Global Magnitsky sanctions for technology companies that have enabled human rights abuses, including the arrests, disappearance, torture and murder of human rights activists and journalists, such as Jamal Khashoggi, by selling powerful surveillance technology to authoritarian governments,” says the letter.
18 Democratic senators and members of congress signed the letter, led by Adam Schiff (CA), Chairman of the House Permanent Select Committee on Intelligence; Gregory Meeks (NY), Chairman of the House Foreign Affairs Committee; Carolyn B. Maloney (NY), Chairwoman of the Committee on Oversight and Reform; And Ron Wyden (OR), Chairman of the Senate Committee on Finance.
And speaking of Oregon: according to the Associated Press, Oregon’s Treasurer Tobias Read is exploring legal options to terminate connections with NSO group, in it is invested via $233 million of the state employee retirement fund (via majority share owner, Novalpina Capital).
"Oregon's pension fund should not support companies like NSO, which the Biden administration recently confirmed has enabled authoritarian regimes to target journalists and human rights advocates," Wyden was quoted saying.
Spyware traces found on more activists’ phones
And there’s more: according to Israel’s Channel 12, Zoom decided to cut business ties with NSO. The company issued a statement in response, stating that “NSO decided several months ago to begin using a different and secure service that allows conference calls, video calls and more”, adding “there is no connection between between the company being put on any list and the transition that took place several months earlier.” Jeffries Financial Group has apparently also decided to resign as loan agent for NSO – which is already in danger of insolvency.
On top of all that, the Guardian reported that Pegasus was used on the phone of Indian activist Rona Wilson, a well-known prisoners’ rights activist and vocal critic of Prime Minister Narendra Modi. Forensic analysis by Amnesty International’s Security Lab (which just 10 days ago discovered that four Kazakh activists were also targeted), showed digital traces of the spyware.
Wilson has been incarcerated since 2018 due to terror-related charges. His number appeared on the global list of over 50 thousand phone numbers leaked earlier this year, which allegedly show the connection between NSO clients and potential targets, or at least people of interest.
A second Guardian report, published yesterday (Monday) claims that Pegasus was used to spy on a UN-backed investigator probing potential war crimes violations in Yemen, a Tunisian human rights activist named Kamel Jendoubi. And overnight, AP reported that two prominent Polish opposition figures, attorney Roman Giertych and prosecutor Ewa Wrzosek, also had their phones hacked by the spyware.
In light of all of this (and everything else that has happened in recent months), reports that NSO is considering nixing the Pegasus division and putting itself up for sale, should come as no surprise.



