Kaspersky researchers link new ransomware to 'Lazarus', a North Korean APT group
The move by Lazarus to create and distribute ransomware signifies a worrisome change of strategy to pursue cyber attacks for financial gain
Lidar Gravé-Lazi
|
28/07/2020
Kaspersky researchers have traced VHD ransomware, first discussed in public in the Spring of 2020, to Lazarus, a prominent North-Korean APT group, the company announced on Tuesday.
According to Kaspersky, the move by Lazarus to create and distribute ransomware, signifies a change of strategy and indicates a readiness to pursue cyber attacks for financial gain, which researchers say is highly unusual among state-sponsored APT groups.
In March and April 2020, a few cybersecurity organizations, including Kaspersky, reported on VHD ransomware – a malicious program designed to extort money from its victims, which stood out due to its self-replication method.
While, at the time, the actor behind the attacks was not determined, Kaspersky researchers linked the VHD ransomware to Lazarus with high confidence following analysis of an incident where it was used in close conjunction with known Lazarus tools against businesses in France and Asia.
“We have known that Lazarus has always been focused on financial gain, however, since WannaCry we had not really seen any engagement with ransomware. While it is obvious that the group cannot match the efficiency of other cybercriminal gangs with this hit-and-run approach to targeted ransomware, the fact that it has turned to such types of attacks is worrisome," said Ivan Kwiatkowski, senior security researcher at Kaspersky’s GReAT.
He added: "The global ransomware threat is big enough as it is, and often has significant financial implications for victim organizations up to the point of rendering them bankrupt. The question we have to ask ourselves is whether these attacks are an isolated experiment or part of a new trend and, consequently, whether private companies have to worry about becoming victims of state-sponsored threat actors.”
According to Kaspersky researchers, two separate investigations involving VHD ransomware were conducted between March and May 2020 - the first in Europe, which did not provide many hints as to who was behind it.
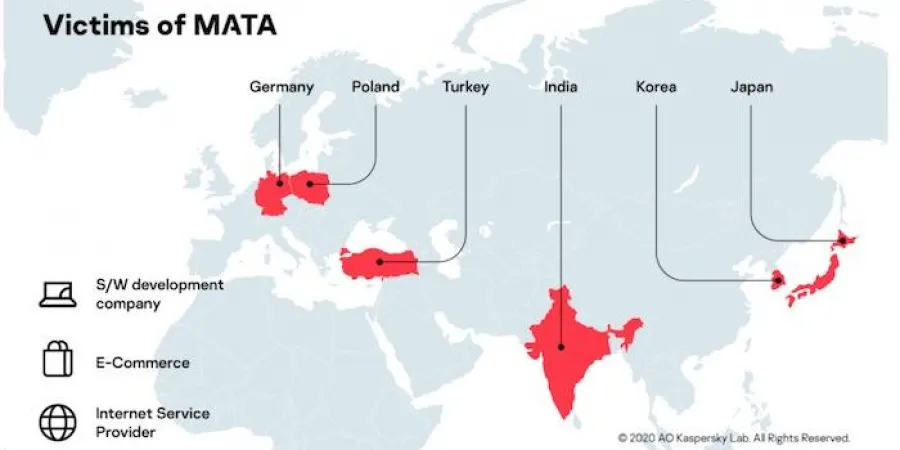
The second incident provided more clues that enabled the researchers to link the ransomware to Lazarus. Among other things, the attackers used a backdoor, which was a part of a multiplatform framework called MATA, which Kaspersky recently uncovered and is linked to the same threat actor due to a number of code and utility similarities.
The established connection indicated that Lazarus was behind the VHD ransomware campaigns that have been documented so far. Kaspersky researchers noted that this is also the first time it has been established that the Lazarus group has resorted to targeted ransomware attacks for financial gain, having created and solely operated its own ransomware, which is not typical in the cybercrime ecosystem.
The move by Lazarus to create and distribute ransomware signifies a worrisome change of strategy to pursue cyber attacks for financial gain
Kaspersky researchers have traced VHD ransomware, first discussed in public in the Spring of 2020, to Lazarus, a prominent North-Korean APT group, the company announced on Tuesday.
According to Kaspersky, the move by Lazarus to create and distribute ransomware, signifies a change of strategy and indicates a readiness to pursue cyber attacks for financial gain, which researchers say is highly unusual among state-sponsored APT groups.
In March and April 2020, a few cybersecurity organizations, including Kaspersky, reported on VHD ransomware – a malicious program designed to extort money from its victims, which stood out due to its self-replication method.
While, at the time, the actor behind the attacks was not determined, Kaspersky researchers linked the VHD ransomware to Lazarus with high confidence following analysis of an incident where it was used in close conjunction with known Lazarus tools against businesses in France and Asia.
“We have known that Lazarus has always been focused on financial gain, however, since WannaCry we had not really seen any engagement with ransomware. While it is obvious that the group cannot match the efficiency of other cybercriminal gangs with this hit-and-run approach to targeted ransomware, the fact that it has turned to such types of attacks is worrisome," said Ivan Kwiatkowski, senior security researcher at Kaspersky’s GReAT.
He added: "The global ransomware threat is big enough as it is, and often has significant financial implications for victim organizations up to the point of rendering them bankrupt. The question we have to ask ourselves is whether these attacks are an isolated experiment or part of a new trend and, consequently, whether private companies have to worry about becoming victims of state-sponsored threat actors.”
According to Kaspersky researchers, two separate investigations involving VHD ransomware were conducted between March and May 2020 - the first in Europe, which did not provide many hints as to who was behind it.
The second incident provided more clues that enabled the researchers to link the ransomware to Lazarus. Among other things, the attackers used a backdoor, which was a part of a multiplatform framework called MATA, which Kaspersky recently uncovered and is linked to the same threat actor due to a number of code and utility similarities.
The established connection indicated that Lazarus was behind the VHD ransomware campaigns that have been documented so far. Kaspersky researchers noted that this is also the first time it has been established that the Lazarus group has resorted to targeted ransomware attacks for financial gain, having created and solely operated its own ransomware, which is not typical in the cybercrime ecosystem.