New Attack Allows Hackers to Run Malicious Code Even After Users Close the Web Page
Ami Rojkes Dombe
| 26/02/2019
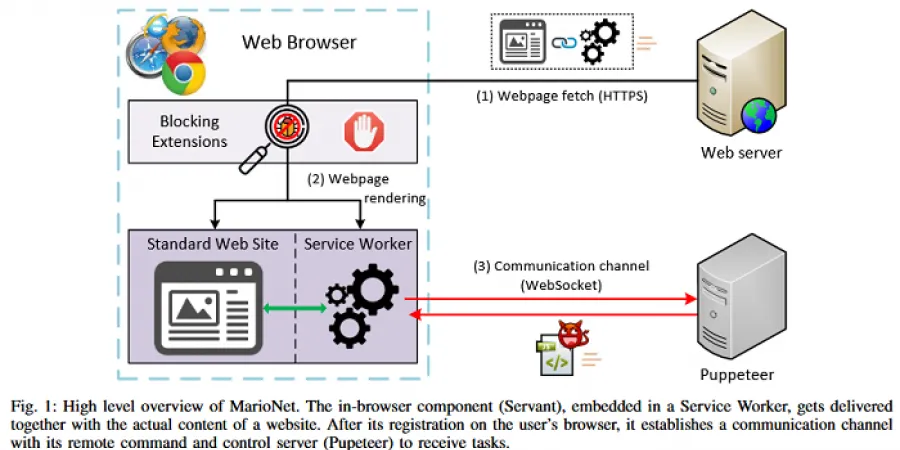
Academics from Greece have developed a new browser-based attack that can allow hackers to run malicious code inside users’ browsers even after users have closed or navigated away from the web page on which they got infected, ZDNet reported. The attack, called MarioNet, uses Service Workers scripts that run separately from visited web pages and in the background.
“Service Workers essentially act as proxy servers that sit between web applications, the browser, and the network (when available). They are intended, among other things, to enable the creation of effective offline experiences, intercept network requests and take appropriate action based on whether the network is available, and update assets residing on the server. They will also allow access to push notifications and background sync APIs.” [Source]
The threat addressed by the Greek researchers is referred to as puppetnets. “Puppetnets rely on websites that coerce web browsers to (unknowingly) participate in malicious activities,” they say.
“Websites controlling puppetnets could be either legitimate sites that have been subverted by attackers, malicious “underground” websites that can lure unsuspected users by providing interesting services (such as free web storage, illegal downloads, etc.), or websites that openly invite users to participate in vigilante campaigns,” according to the research.
“Puppetnets differ from botnets in three fundamental ways,” the researchers explain. “First, puppetnets are not heavily dependent on the exploitation of specific implementation flaws, or on social engineering tactics that trick users into installing malicious software on their computer. They exploit architectural features that serve purposes such as enabling dynamic content, load distribution and cooperation between content providers. At the same time, they rely on the amplification of vulnerabilities that seem insignificant from the perspective of a single browser, but can cause significant damage when abused by a popular website. Thus, it seems harder to eliminate such a threat in similar terms to common implementation flaws, especially if this would require sacrificing functionality that is of great value to web designers. Additionally, even if we optimistically assume that major security problems such as code injection and traditional botnets are successfully countered, some puppetnet attacks will still be possible. Furthermore, the nature of the problem implies that the attack vector is pervasive: puppetnets can instruct any web browser to engage in malicious activities.
“Second, the attacker does not have complete control over the actions of the participating nodes. Instead, actions have to be composed using the primitives offered from within the browser sandbox – hence the analogy to puppets. Although the flexibility of puppetnets seems limited when compared to botnets, we will show that they are surprisingly powerful.
“Finally, participation in puppetnets is dynamic, making them a moving target, since users join and participate unknowingly while surfing the net. Thus, it seems easy for the attackers to maintain a reasonable population, without the burden of having to look for new victims. At the same time, it is harder for the defenders to track and filter out attacks, as puppets are likely to be relatively short-lived.”
Academics from Greece have developed a new browser-based attack that can allow hackers to run malicious code inside users’ browsers even after users have closed or navigated away from the web page on which they got infected, ZDNet reported. The attack, called MarioNet, uses Service Workers scripts that run separately from visited web pages and in the background.
“Service Workers essentially act as proxy servers that sit between web applications, the browser, and the network (when available). They are intended, among other things, to enable the creation of effective offline experiences, intercept network requests and take appropriate action based on whether the network is available, and update assets residing on the server. They will also allow access to push notifications and background sync APIs.” [Source]
The threat addressed by the Greek researchers is referred to as puppetnets. “Puppetnets rely on websites that coerce web browsers to (unknowingly) participate in malicious activities,” they say.
“Websites controlling puppetnets could be either legitimate sites that have been subverted by attackers, malicious “underground” websites that can lure unsuspected users by providing interesting services (such as free web storage, illegal downloads, etc.), or websites that openly invite users to participate in vigilante campaigns,” according to the research.
“Puppetnets differ from botnets in three fundamental ways,” the researchers explain. “First, puppetnets are not heavily dependent on the exploitation of specific implementation flaws, or on social engineering tactics that trick users into installing malicious software on their computer. They exploit architectural features that serve purposes such as enabling dynamic content, load distribution and cooperation between content providers. At the same time, they rely on the amplification of vulnerabilities that seem insignificant from the perspective of a single browser, but can cause significant damage when abused by a popular website. Thus, it seems harder to eliminate such a threat in similar terms to common implementation flaws, especially if this would require sacrificing functionality that is of great value to web designers. Additionally, even if we optimistically assume that major security problems such as code injection and traditional botnets are successfully countered, some puppetnet attacks will still be possible. Furthermore, the nature of the problem implies that the attack vector is pervasive: puppetnets can instruct any web browser to engage in malicious activities.
“Second, the attacker does not have complete control over the actions of the participating nodes. Instead, actions have to be composed using the primitives offered from within the browser sandbox – hence the analogy to puppets. Although the flexibility of puppetnets seems limited when compared to botnets, we will show that they are surprisingly powerful.
“Finally, participation in puppetnets is dynamic, making them a moving target, since users join and participate unknowingly while surfing the net. Thus, it seems easy for the attackers to maintain a reasonable population, without the burden of having to look for new victims. At the same time, it is harder for the defenders to track and filter out attacks, as puppets are likely to be relatively short-lived.”