Eurosatory 2018: BLER Systems to Demonstrate 'Target Profiler' OSINT System
Based on open architecture, BLER’s Target Profiler provides intelligence officers with immediate, actionable intelligence gathered from the Internet, social and cellular networks and Dark Web channels
Eyal Boguslavsky
| 06/06/2018
BLER Systems, a developer of security and cyber intelligence solutions, will demonstrate its Target Profiler OSINT (Open Source Intelligence) System at Eurosatory 2018.
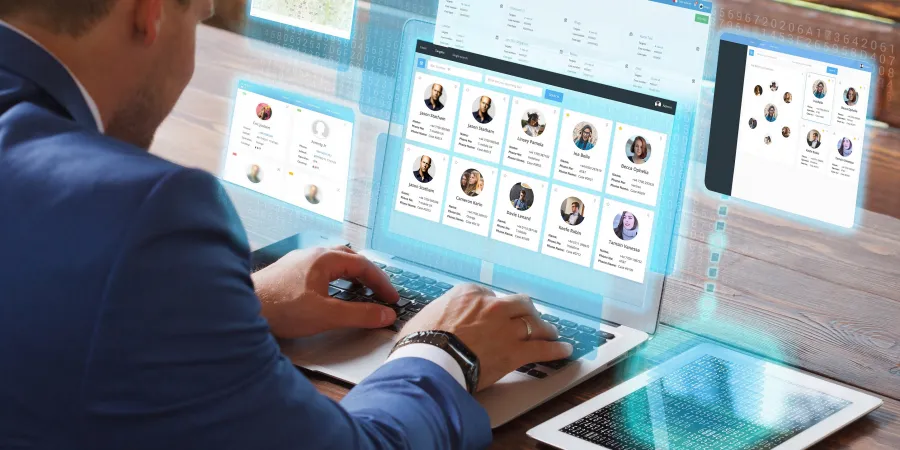
BLER's Target Profiler System is an integrated, enterprise-grade intelligence and investigation-support solution used to conduct business intelligence, and criminal and terror investigations for enterprise organizations, financial institutions, and government agencies.
The system has various configurable capabilities: Link analysis – identifying social connections, similar preferences and common groups between suspects at multiple levels; Sentiment analysis capabilities – analyzing the target’s posts and identifying feelings and word anomalies; Face analytics – identifying the target in multiple pictures captured by a profiling process, including characteristics such as age, race, emotion, whether the suspect is wearing lenses or glasses, and many other unique features; Identifying whether the suspect is already in the system, based on their picture, and indicating a confidence level; Identifying potential activity in Dark Web marketplaces; Indicating on a map the last location of a target, using data collected from social networks and websites; TimeLine – viewing and analyzing all target posts and social network activities, easily finding the most-liked post and all relations between targets according to likes, tagging and comments activity.
“Today, one of the biggest challenges that intelligence officers around the world face every day is the information overload in open channels, how to monitor it and distill from it real intelligence to identify illegal activity,” says Efim Lerner, BLER System’s CTO. “The solution we have developed, which is already being used by intelligence organizations and other customers around the world, is able to automatically and quickly examine huge amounts of information from the Internet, social networks and web applications, and Dark Web channels and to extract from it actionable intelligence. The system is modular, open architecture and scalable and can be very simply adapted by clients to deal with the tasks they require.”
Based on open architecture, BLER’s Target Profiler provides intelligence officers with immediate, actionable intelligence gathered from the Internet, social and cellular networks and Dark Web channels
BLER Systems, a developer of security and cyber intelligence solutions, will demonstrate its Target Profiler OSINT (Open Source Intelligence) System at Eurosatory 2018.
BLER's Target Profiler System is an integrated, enterprise-grade intelligence and investigation-support solution used to conduct business intelligence, and criminal and terror investigations for enterprise organizations, financial institutions, and government agencies.
The system has various configurable capabilities: Link analysis – identifying social connections, similar preferences and common groups between suspects at multiple levels; Sentiment analysis capabilities – analyzing the target’s posts and identifying feelings and word anomalies; Face analytics – identifying the target in multiple pictures captured by a profiling process, including characteristics such as age, race, emotion, whether the suspect is wearing lenses or glasses, and many other unique features; Identifying whether the suspect is already in the system, based on their picture, and indicating a confidence level; Identifying potential activity in Dark Web marketplaces; Indicating on a map the last location of a target, using data collected from social networks and websites; TimeLine – viewing and analyzing all target posts and social network activities, easily finding the most-liked post and all relations between targets according to likes, tagging and comments activity.
“Today, one of the biggest challenges that intelligence officers around the world face every day is the information overload in open channels, how to monitor it and distill from it real intelligence to identify illegal activity,” says Efim Lerner, BLER System’s CTO. “The solution we have developed, which is already being used by intelligence organizations and other customers around the world, is able to automatically and quickly examine huge amounts of information from the Internet, social networks and web applications, and Dark Web channels and to extract from it actionable intelligence. The system is modular, open architecture and scalable and can be very simply adapted by clients to deal with the tasks they require.”