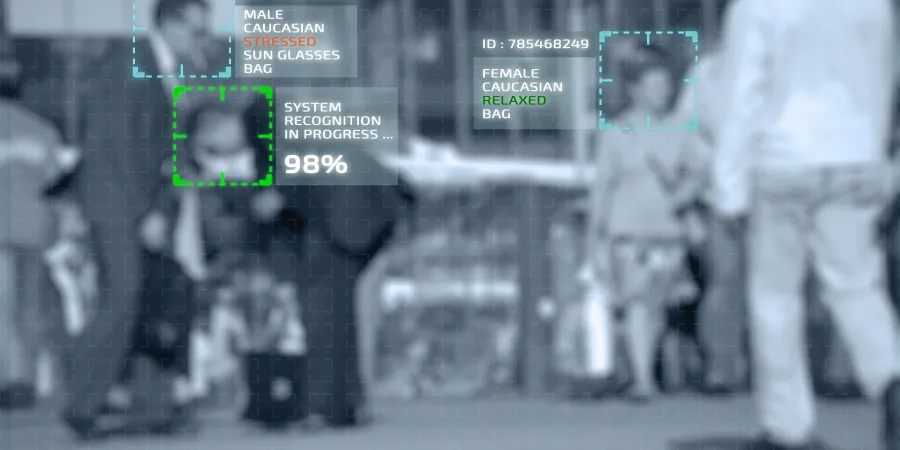
Overcoming the New "Bio-Hazards" of the Spying Game
One of the greatest paradoxes of the security world is the fact that anything that is good for terrorists is good for spies as well. One element wants to do evil, the other wants to do good, but as far as the technological aspect is concerned, both are expected to be harmed by the implementation of biometric identification monitoring technologies in the municipal domain
Ami Rojkes Dombe
| 03/08/2018
Dawn Meyerriecks, Deputy Director of the CIA's Science & Technology Division, recently told CNN that "Digital surveillance, including closed-circuit television and wireless infrastructure in about 30 countries is so good that physical tracking is no longer necessary, but the CIA is spying back.
"As of six months ago, the Agency has been pursuing nearly 140 artificial intelligence projects. That way, agents can try to figure out where they are being surveilled and how they might evade the camera eye. Social media and digital tracking in cell phones and other pieces of technology also present a problem. That is forcing CIA officials to 'live their cover' even more than before, and take steps to trick the digital trackers. Maybe the data says 'you went to see a movie with your family,' but maybe that's not where you actually are. It'll look like your normal pattern of life."
Meyerriecks' statements should not come as a surprise to anyone following the evolution of biometric identification technology and the implementation thereof in the municipal domain. China has recently introduced a special certificate for civilians specifying which activities they will be allowed to engage in, in the digital space. In addition, Beijing and other cities were provided with extensive networks of surveillance cameras fitted with facial recognition software modules. The European Union intends to demand that its inhabitants acquire a biometric identity, which includes fingerprints on their identity cards, while at the same time implementing a biometric identification database of persons entering and leaving Europe.
What's Good for Terrorists is Good for Spies
One of the greatest paradoxes of the security world is the fact that anything that is good for terrorists is good for spies as well. In both cases, the elements concerned wish to remain anonymous or continue to operate under a false identity, to evade surveillance, meet with other people apparently at random, maintain secret caches for the transfer of information and travel freely while carrying weapons or explosives across borders and between urban centers without being detected.
One of these elements wants to do evil, the other wants to do good, but as far as the technological aspect is concerned, both are expected to be harmed by the implementation of biometric identification monitoring technologies in the municipal domain
The objective of these monitoring technologies is to provide police and internal security forces with more effective control over the internal space of the state. Systems incorporating these technologies are currently being deployed along various borders.
The First Loop: States have deployed surveillance and monitoring systems along their external (sea or land) borders. These systems utilize Radar and electro-optical sensors primarily. More recently, attempts have been made to incorporate an additional layer of biometric identification over these sensors.
The Second Loop: Some states want to deploy surveillance and monitoring technologies at their points of entrance and exit – seaports, airports, and land border crossing points.
The Third Loop: Systems incorporating these technologies are deployed in city centers and along transportation routes.
The Fourth Loop: Systems incorporating these technologies are deployed around specific individuals "illuminated" or "marked" by the internal security services.
The data produced by all of the above surveillance and monitoring loops is sent to a central command and control complex, where it is analyzed by algorithms and human analysts. The information gained from that data is translated into focused research questions that make it possible to have the surveillance and monitoring infrastructure focus on specific targets.
Modern surveillance and monitoring setups provide a large number of surveillance "dimensions" – one basic surveillance dimension operating continuously around the clock, plus many other focused dimensions that help the user find spies, terrorists, criminals and various other elements.
Adjustment Period
For the intelligence services, the introduction of these technologies has created a new reality that must be adjusted to. The solutions may be divided into several primary courses of action.
The first course of action involves the databases. Simplified, biometric identification systems operate on the basis of a comparative verification between a server that stores the biometric database and an end device that samples the subject. In the event that the subject's data correlate with the data in the database, an alert will be issued. An intelligence organization interested in allowing its agents to operate freely would like to plant their biometric identification data in various databases along with a false identity. In this way, the system will identify David as Moses, and Moses will be free to travel through the state in a perfectly legitimate manner.
One of the challenges in this context involves a situation where the biometric identification databases of different countries are interconnected. If David had been registered as Moses in a certain country, but used the same biometric identification sample to register as Avishai in another country, and the databases of those two countries are interconnected, an alert will be issued to the effect that the sample should be examined – and that could "burn" the agent in question. On the other hand, a biometric identification sample is univalent, so if David had registered as Moses, he would always remain Moses.
To solve this problem, the intelligence organization will have to plant a sample with a certain identity, and any subsequent change of that identity would require a complete erasure of the history of that identity and the creation of a new identity using the same biometric identification sample. Changing the sample management system to a blockchain infrastructure can make things even more difficult, as such a transition will make it impossible to delete or alter an identity associated with a biometric identification sample.
The second course of action involves handling of the monitoring devices themselves and their communication networks. Using this course of action, the intelligence organization can disrupt the operation of communication networks while synchronizing that disruption with the operations of its agents in the areas of interest. Surveillance cameras, IoT sensors, and other sensors are all eventually connected to a communication network. Most of these devices are connected to a landline or wireless network. In the future, devices utilizing a satellite connection may be used as well. In any case, accessing the communication networks and disrupting them or setting up an EW jamming envelope around the area where an agent operates could mask the monitoring activity covering that agent, at least temporarily.
Handling the devices themselves can achieve the same result. Some of the devices are installed in the physical space and consequently are accessible to agents wishing to alter their software or damage them in a manner that would render monitoring impossible. Another option involves the establishment of bogus maintenance companies and winning contracts that would enable the intelligence organization to become the de-facto legitimate operator of the monitoring setup in a certain area. In this way, the operation of the monitoring devices may be disrupted legally and legitimately.
The third course of action involves the use of physical measures in order to evade digital surveillance. Surveillance cameras, volumetric monitoring, locating devices, smartphones or any other monitoring or tracking device are all based on technology and can be duped. Hats may be worn to conceal one's facial features. Special suits may be worn to evade infrared surveillance cameras. Change of clothes, make-up, masks, etc. may all be used to evade surveillance. Attempts to evade surveillance are not confined to intelligence organizations, and a search of commercial websites worldwide will produce numerous products in this category. Intelligence organizations employ various specialists and maintain contact with engineers from defense industries, so they can invent for themselves a range of physical or virtual devices and applications for evading digital surveillance.
The fourth course of action involves overloading the surveillance setups (establishing a false routine). If anything can cause an analyst at an operations center to stop monitoring his or her targets – false alarms can. An intelligence organization can take advantage of this fact and overload the surveillance systems in the areas where it operates to the point where the sensitivity threshold of the analyst will be sufficiently low to enable the intelligence organization to stage real incidents that would go undetected.
Another aspect involves one of the inherent weaknesses of some digital surveillance systems – the search for irregular behavior. These systems study, over a certain period of time, the behavior patterns of a controlled area, or a controlled individual, and come up with a routine threshold. Any deviation from that routine threshold will issue an alert. If there is no deviation – no alert will be generated. Changing this threshold intentionally can generate "white noise" that would provide a sufficient degree of freedom to engage in espionage activity.
There is no doubt that the introduction of biometric identification technologies to the security, surveillance and monitoring loops makes life much more difficult for the intelligence services. At the same time, changes in agent training, employing cyber warfare units against the data storage, verification, and traffic infrastructure, along with artificial intelligence tools, can provide a sufficient degree of freedom to enable intelligence collection operations even in countries regarded as technologically advanced.
One of the greatest paradoxes of the security world is the fact that anything that is good for terrorists is good for spies as well. One element wants to do evil, the other wants to do good, but as far as the technological aspect is concerned, both are expected to be harmed by the implementation of biometric identification monitoring technologies in the municipal domain
Dawn Meyerriecks, Deputy Director of the CIA's Science & Technology Division, recently told CNN that "Digital surveillance, including closed-circuit television and wireless infrastructure in about 30 countries is so good that physical tracking is no longer necessary, but the CIA is spying back.
"As of six months ago, the Agency has been pursuing nearly 140 artificial intelligence projects. That way, agents can try to figure out where they are being surveilled and how they might evade the camera eye. Social media and digital tracking in cell phones and other pieces of technology also present a problem. That is forcing CIA officials to 'live their cover' even more than before, and take steps to trick the digital trackers. Maybe the data says 'you went to see a movie with your family,' but maybe that's not where you actually are. It'll look like your normal pattern of life."
Meyerriecks' statements should not come as a surprise to anyone following the evolution of biometric identification technology and the implementation thereof in the municipal domain. China has recently introduced a special certificate for civilians specifying which activities they will be allowed to engage in, in the digital space. In addition, Beijing and other cities were provided with extensive networks of surveillance cameras fitted with facial recognition software modules. The European Union intends to demand that its inhabitants acquire a biometric identity, which includes fingerprints on their identity cards, while at the same time implementing a biometric identification database of persons entering and leaving Europe.
What's Good for Terrorists is Good for Spies
One of the greatest paradoxes of the security world is the fact that anything that is good for terrorists is good for spies as well. In both cases, the elements concerned wish to remain anonymous or continue to operate under a false identity, to evade surveillance, meet with other people apparently at random, maintain secret caches for the transfer of information and travel freely while carrying weapons or explosives across borders and between urban centers without being detected.
One of these elements wants to do evil, the other wants to do good, but as far as the technological aspect is concerned, both are expected to be harmed by the implementation of biometric identification monitoring technologies in the municipal domain
The objective of these monitoring technologies is to provide police and internal security forces with more effective control over the internal space of the state. Systems incorporating these technologies are currently being deployed along various borders.
The First Loop: States have deployed surveillance and monitoring systems along their external (sea or land) borders. These systems utilize Radar and electro-optical sensors primarily. More recently, attempts have been made to incorporate an additional layer of biometric identification over these sensors.
The Second Loop: Some states want to deploy surveillance and monitoring technologies at their points of entrance and exit – seaports, airports, and land border crossing points.
The Third Loop: Systems incorporating these technologies are deployed in city centers and along transportation routes.
The Fourth Loop: Systems incorporating these technologies are deployed around specific individuals "illuminated" or "marked" by the internal security services.
The data produced by all of the above surveillance and monitoring loops is sent to a central command and control complex, where it is analyzed by algorithms and human analysts. The information gained from that data is translated into focused research questions that make it possible to have the surveillance and monitoring infrastructure focus on specific targets.
Modern surveillance and monitoring setups provide a large number of surveillance "dimensions" – one basic surveillance dimension operating continuously around the clock, plus many other focused dimensions that help the user find spies, terrorists, criminals and various other elements.
Adjustment Period
For the intelligence services, the introduction of these technologies has created a new reality that must be adjusted to. The solutions may be divided into several primary courses of action.
The first course of action involves the databases. Simplified, biometric identification systems operate on the basis of a comparative verification between a server that stores the biometric database and an end device that samples the subject. In the event that the subject's data correlate with the data in the database, an alert will be issued. An intelligence organization interested in allowing its agents to operate freely would like to plant their biometric identification data in various databases along with a false identity. In this way, the system will identify David as Moses, and Moses will be free to travel through the state in a perfectly legitimate manner.
One of the challenges in this context involves a situation where the biometric identification databases of different countries are interconnected. If David had been registered as Moses in a certain country, but used the same biometric identification sample to register as Avishai in another country, and the databases of those two countries are interconnected, an alert will be issued to the effect that the sample should be examined – and that could "burn" the agent in question. On the other hand, a biometric identification sample is univalent, so if David had registered as Moses, he would always remain Moses.
To solve this problem, the intelligence organization will have to plant a sample with a certain identity, and any subsequent change of that identity would require a complete erasure of the history of that identity and the creation of a new identity using the same biometric identification sample. Changing the sample management system to a blockchain infrastructure can make things even more difficult, as such a transition will make it impossible to delete or alter an identity associated with a biometric identification sample.
The second course of action involves handling of the monitoring devices themselves and their communication networks. Using this course of action, the intelligence organization can disrupt the operation of communication networks while synchronizing that disruption with the operations of its agents in the areas of interest. Surveillance cameras, IoT sensors, and other sensors are all eventually connected to a communication network. Most of these devices are connected to a landline or wireless network. In the future, devices utilizing a satellite connection may be used as well. In any case, accessing the communication networks and disrupting them or setting up an EW jamming envelope around the area where an agent operates could mask the monitoring activity covering that agent, at least temporarily.
Handling the devices themselves can achieve the same result. Some of the devices are installed in the physical space and consequently are accessible to agents wishing to alter their software or damage them in a manner that would render monitoring impossible. Another option involves the establishment of bogus maintenance companies and winning contracts that would enable the intelligence organization to become the de-facto legitimate operator of the monitoring setup in a certain area. In this way, the operation of the monitoring devices may be disrupted legally and legitimately.
The third course of action involves the use of physical measures in order to evade digital surveillance. Surveillance cameras, volumetric monitoring, locating devices, smartphones or any other monitoring or tracking device are all based on technology and can be duped. Hats may be worn to conceal one's facial features. Special suits may be worn to evade infrared surveillance cameras. Change of clothes, make-up, masks, etc. may all be used to evade surveillance. Attempts to evade surveillance are not confined to intelligence organizations, and a search of commercial websites worldwide will produce numerous products in this category. Intelligence organizations employ various specialists and maintain contact with engineers from defense industries, so they can invent for themselves a range of physical or virtual devices and applications for evading digital surveillance.
The fourth course of action involves overloading the surveillance setups (establishing a false routine). If anything can cause an analyst at an operations center to stop monitoring his or her targets – false alarms can. An intelligence organization can take advantage of this fact and overload the surveillance systems in the areas where it operates to the point where the sensitivity threshold of the analyst will be sufficiently low to enable the intelligence organization to stage real incidents that would go undetected.
Another aspect involves one of the inherent weaknesses of some digital surveillance systems – the search for irregular behavior. These systems study, over a certain period of time, the behavior patterns of a controlled area, or a controlled individual, and come up with a routine threshold. Any deviation from that routine threshold will issue an alert. If there is no deviation – no alert will be generated. Changing this threshold intentionally can generate "white noise" that would provide a sufficient degree of freedom to engage in espionage activity.
There is no doubt that the introduction of biometric identification technologies to the security, surveillance and monitoring loops makes life much more difficult for the intelligence services. At the same time, changes in agent training, employing cyber warfare units against the data storage, verification, and traffic infrastructure, along with artificial intelligence tools, can provide a sufficient degree of freedom to enable intelligence collection operations even in countries regarded as technologically advanced.