Check Point Reveals New Attack Vector: Malicious Subtitle Files
Ami Rojkes Dombe
| 23/05/2017
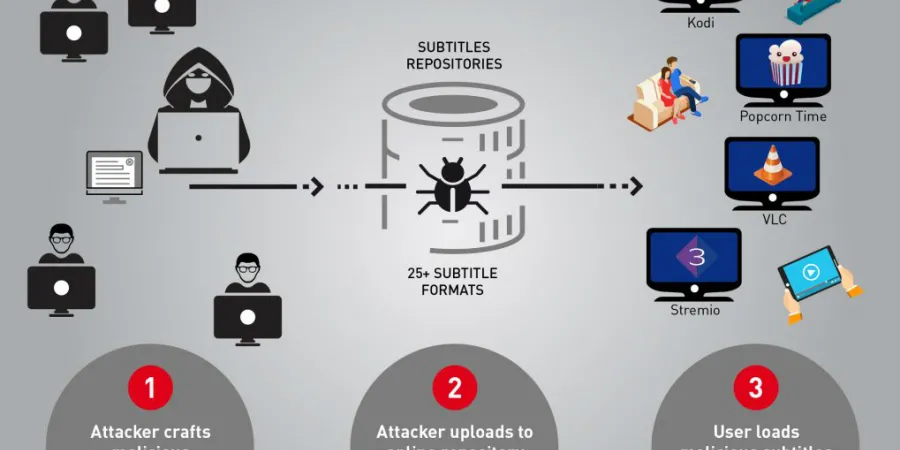
Check Point researchers revealed a new attack vector which threatens millions of users worldwide – attack by subtitles. By crafting malicious subtitle files, which are then downloaded by a victim’s media player, attackers can take complete control over any type of device via vulnerabilities found in many popular streaming platforms, including VLC, Kodi (XBMC), Popcorn-Time and strem.io. According to Check Point's report, there are approximately 200 million video players and streamers that currently run the vulnerable software, making this one of the most widespread, easily accessed and zero-resistance vulnerability reported in recent years.
Perpetrators use various methods, also referred to as ‘attack vectors,' to deliver cyberattacks. These attack vectors can be divided into two major categories: Either the attacker persuades the user to visit a malicious website, or he tricks him into running a malicious file on his computer.
Check Point research reveals a new possible attack vector, using a completely overlooked technique in which the cyberattack is delivered when movie subtitles are loaded by the user’s media player. These subtitles repositories are, in practice, treated as a trusted source by the user or media player. The company also revealed that those repositories can be manipulated and be made to award the attacker’s malicious subtitles a high score, which results in those specific subtitles being served to the user. This method requires little or no deliberate action on the part of the user, making it all the more dangerous.
Unlike traditional attack vectors, which security firms and users are widely aware of, movie subtitles are perceived as nothing more than benign text files. This means users, Anti-Virus software, and other security solutions vet them without trying to assess their real nature, leaving millions of users exposed to this risk.
The attack vector relies heavily on the poor state of security in the way various media players process subtitle files and the large number of subtitle formats. To begin with, there are over 25 subtitle formats in use, each with unique features and capabilities. Media players often need to parse together multiple subtitle formats to ensure coverage and provide a better user experience, with each media player using a different method. Like other, similar situations which involve fragmented software, this results in numerous distinct vulnerabilities.
The total number of the affected users is in the hundreds of millions. Each of the media players found to be vulnerable to date has millions of users, and Check Point estimates that other media players could be vulnerable to similar attacks as well. VLC has over 170 million downloads of its latest version alone, which was released June 5, 2016. Kodi (XBMC) has reached over 10 million unique users per day, and nearly 40 million unique users each month. No current estimates exist for Popcorn Time usage, but it’s safe to assume that the number is likewise in the millions.
By conducting attacks through subtitles, hackers can take complete control over any device running them. From this point on, the attacker can do whatever he wants with the victim’s machine, whether it is a PC, a smart TV, or a mobile device. The potential damage the attacker can inflict is endless, ranging anywhere from stealing sensitive information, installing ransomware, mass Denial of Service attacks, and much more.
To date, Check Point tested and found vulnerabilities in four of the most prominent media players: VLC, Kodi, Popcorn Time and Stremio. There is a reason to believe similar vulnerabilities exist in other media players as well. Some of the issues were already fixed, while others are still under investigation.
Platforms Update:
PopcornTime – https://ci.popcorntime.sh/job/Popcorn-Time-Desktop/249
Kodi – https://github.com/xbmc/xbmc/pull/12024)
VLC – http://get.videolan.org/vlc/2.2.5.1/win32/vlc-2.2.5.1-win32.exe
Stremio https://megahexandword.com/rnw_H8hGnAaWDkyg
IPS Signatures:
Popcorn Time Subtitles Remote Code Execution
Kodi Open Subtitles Addon Remote Code Execution
VLC ParseJSS Null Skip Subtitle Remote Code Execution
Stremio Subtitles Remote Code Execution
[Source: Check Point's Blog]
Check Point researchers revealed a new attack vector which threatens millions of users worldwide – attack by subtitles. By crafting malicious subtitle files, which are then downloaded by a victim’s media player, attackers can take complete control over any type of device via vulnerabilities found in many popular streaming platforms, including VLC, Kodi (XBMC), Popcorn-Time and strem.io. According to Check Point's report, there are approximately 200 million video players and streamers that currently run the vulnerable software, making this one of the most widespread, easily accessed and zero-resistance vulnerability reported in recent years.
Perpetrators use various methods, also referred to as ‘attack vectors,' to deliver cyberattacks. These attack vectors can be divided into two major categories: Either the attacker persuades the user to visit a malicious website, or he tricks him into running a malicious file on his computer.
Check Point research reveals a new possible attack vector, using a completely overlooked technique in which the cyberattack is delivered when movie subtitles are loaded by the user’s media player. These subtitles repositories are, in practice, treated as a trusted source by the user or media player. The company also revealed that those repositories can be manipulated and be made to award the attacker’s malicious subtitles a high score, which results in those specific subtitles being served to the user. This method requires little or no deliberate action on the part of the user, making it all the more dangerous.
Unlike traditional attack vectors, which security firms and users are widely aware of, movie subtitles are perceived as nothing more than benign text files. This means users, Anti-Virus software, and other security solutions vet them without trying to assess their real nature, leaving millions of users exposed to this risk.
The attack vector relies heavily on the poor state of security in the way various media players process subtitle files and the large number of subtitle formats. To begin with, there are over 25 subtitle formats in use, each with unique features and capabilities. Media players often need to parse together multiple subtitle formats to ensure coverage and provide a better user experience, with each media player using a different method. Like other, similar situations which involve fragmented software, this results in numerous distinct vulnerabilities.
The total number of the affected users is in the hundreds of millions. Each of the media players found to be vulnerable to date has millions of users, and Check Point estimates that other media players could be vulnerable to similar attacks as well. VLC has over 170 million downloads of its latest version alone, which was released June 5, 2016. Kodi (XBMC) has reached over 10 million unique users per day, and nearly 40 million unique users each month. No current estimates exist for Popcorn Time usage, but it’s safe to assume that the number is likewise in the millions.
By conducting attacks through subtitles, hackers can take complete control over any device running them. From this point on, the attacker can do whatever he wants with the victim’s machine, whether it is a PC, a smart TV, or a mobile device. The potential damage the attacker can inflict is endless, ranging anywhere from stealing sensitive information, installing ransomware, mass Denial of Service attacks, and much more.
To date, Check Point tested and found vulnerabilities in four of the most prominent media players: VLC, Kodi, Popcorn Time and Stremio. There is a reason to believe similar vulnerabilities exist in other media players as well. Some of the issues were already fixed, while others are still under investigation.
Platforms Update:
PopcornTime – https://ci.popcorntime.sh/job/Popcorn-Time-Desktop/249
Kodi – https://github.com/xbmc/xbmc/pull/12024)
VLC – http://get.videolan.org/vlc/2.2.5.1/win32/vlc-2.2.5.1-win32.exe
Stremio https://megahexandword.com/rnw_H8hGnAaWDkyg
IPS Signatures:
Popcorn Time Subtitles Remote Code Execution
Kodi Open Subtitles Addon Remote Code Execution
VLC ParseJSS Null Skip Subtitle Remote Code Execution
Stremio Subtitles Remote Code Execution
[Source: Check Point's Blog]